Enhance business security
Penetration Testing Services
With penetration testing services, your business can enhance security across your computer network. Exposing core vulnerabilities with scheduled simulated attacks discovers weak spots, which can be addressed to ensure long-term protection. Enquire now to stop cyberattacks.
The tests simulate different types of attacks, including SQL injection, denial of service (DoS), and man-in-the-middle (MiTM). By finding vulnerabilities, analysts can assess a company’s security measures and provide an improvement plan.

A CHECK and CREST accredited penetration testing company
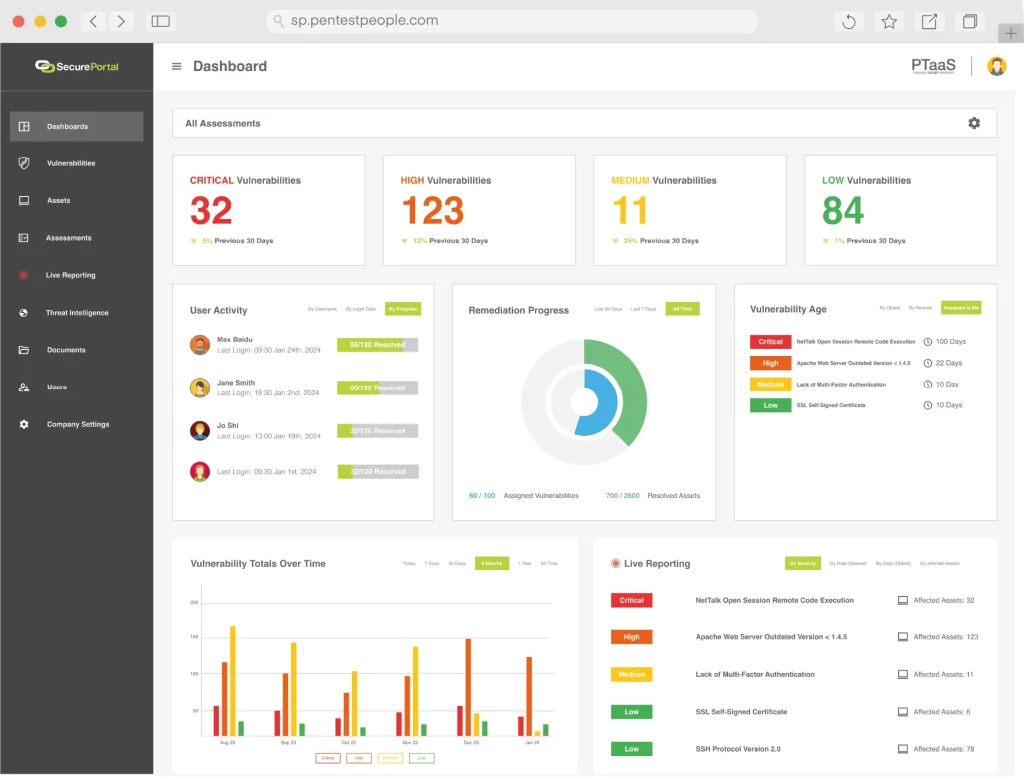
We offer a comprehensive range of services using industry leading techniques and methods, tailored to meet the unique security needs of any business. Unlike other penetration testing companies in the UK, we deliver results through SecurePortal, replacing traditional PDF reports with real-time, interactive dashboards for a faster, more efficient, and secure experience.
Through the portal, users can monitor vulnerabilities dynamically, prioritising risks and managing security improvements efficiently. Our penetration testing solutions also include a Vulnerability Platform that provides real-time visibility, automated scans, and continuous monitoring for seamless risk management.
Our innovative Vulnerability Platform offers real time visibility, automated scans and continuous monitoring for seamless and efficient vulnerability management. We also offer live reporting, which lets you fix issues in real time, saving time and reducing risk.
We’re CHECK and CREST accredited, and we hold ISO 27001 and ISO 9001, as well as being certified cyber essential assessors. Our experienced CHECK team consists of 16 experts, with 5 of them being CHECK team leaders, who are among the first in the UK to achieve principal or chartered status under the new industry registration process.

The types of penetration testing
Different businesses require different cyber security solutions. Choose from a range of options to match your company’s needs, removing the guesswork from your security protocols.
Infrastructure Penetration Testing is designed to identify and address vulnerabilities across your network, servers, and critical systems before they can be exploited by attackers. This service offers several benefits, including uncovering hidden vulnerabilities that may otherwise go unnoticed, improving your security posture by providing insights into your system’s strengths and weaknesses, and preventing future breaches by simulating real-world attacks to assess your system’s ability to defend against various cyber threats.
Web Application Penetration Testing focuses on identifying and remediating vulnerabilities within web applications, such as SQL injection, cross-site scripting (XSS), and authentication flaws. The benefits of this service include identifying critical security vulnerabilities before attackers can exploit them, exposing logic flaws and insecure functionalities such as broken authentication or session management issues. By addressing these vulnerabilities, the service not only enhances the security of your application but also helps protect both users and your business’s reputation, preventing potential data breaches, unauthorised access, and downtime that could lead to significant financial and reputational damage.
Mobile Application Penetration Testing is tailored to assess vulnerabilities in iOS and Android applications. This service helps uncover security weaknesses, including insecure data storage, API vulnerabilities, and encryption flaws, which attackers could exploit. The key benefits include identifying critical security vulnerabilities before attackers can exploit them, exposing insecure functionalities such as broken authentication or session management issues, and safeguarding both users and your business by preventing breaches and minimising the risk of reputational harm.
IT Health Check (ITHC) is a vital security audit for companies seeking access to the Public Services Network (PSN). This service identifies vulnerabilities across networks, infrastructures, and critical systems while ensuring compliance with PSN security standards. Benefits include enhanced security by protecting sensitive public data from cyber threats, regulatory compliance by meeting PSN standards and gaining access to the secure network, and proactive risk management that offers a clear understanding of your IT environment’s risks, helping to guide security investments.
Cyber Attack Incident Response services provide fast and effective support in the event of a cyber attack or security breach, helping to minimise damage and speed up recovery. These services offer tailored response plans that fit the specific needs of your business, guaranteed response times to reduce downtime, and the option to conduct tabletop exercises to train your team in handling various cyber attack scenarios. By offering these services, businesses can regain control quickly and implement strategies to prevent future attacks.
Cloud Penetration Testing focuses on assessing cloud environments for vulnerabilities, including misconfigurations, access control weaknesses, and issues with APIs or data storage. The benefits include enhanced business data protection by identifying and addressing potential vulnerabilities before they are exploited, ensuring compliance with industry regulations, and strengthening customer trust by demonstrating a commitment to safeguarding sensitive information stored in the cloud.
Every business has unique security requirements and the right type of penetration testing depends on factors such as industry, infrastructure, compliance needs, and risk exposure. A tailored testing approach ensures your organisation quickly identifies and mitigates vulnerabilities before cyber threats exploit them.
Feature
Lite
Professional
Feature
Feature
Feature
Feature
A bulletproof penetration testing process
IT penetration testing for businesses follows a structured and thorough process to identify security vulnerabilities, assess risks, and provide actionable remediation strategies. Our approach ensures that businesses can strengthen their cyber security posture against potential threats. Below is a step-by-step breakdown of how we conduct penetration tests.
- Identifying the assets to be tested (e.g., web applications, networks, APIs, cloud infrastructure).
- Understanding compliance requirements and business objectives.
- Determining the type of penetration test needed (internal, external, red teaming, etc.).
- Establishing test boundaries to ensure minimal disruption to your operations.
- Passive and active reconnaissance using open-source intelligence (OSINT).
- Identifying publicly available data that could be exploited.
- Scanning for potential entry points using automated tools and manual techniques.
- Scanning for known vulnerabilities using frameworks like OWASP, CVE databases, and custom scripts.
- Assessing misconfigurations, outdated software, and weak credentials.
- Prioritising vulnerabilities based on exploitability and potential impact.
- Attempting to bypass security controls.
- Gaining unauthorised access to sensitive data.
- Testing privilege escalation scenarios.
- Conducting lateral movement within the network to assess internal risks.
- Determining the depth of system compromise.
- Identifying potential data breaches or unauthorised system control.
- Simulating advanced persistent threats (APTs) and real-world attack scenarios.
- A technical breakdown of the issues found.
- A risk-based prioritisation matrix.
- Clear, actionable recommendations to mitigate risks.
- An executive summary for non-technical stakeholders.
- Guidance on implementing recommended fixes.
- Q&A sessions with our security experts.
- A retesting phase to validate that vulnerabilities have been successfully patched.
The benefits of working with a penetration testing specialist
Working with WorkNest’s specialists proactive vital extra security by spotting vulnerabilities before they can be exploited, strengthening your defences against new threats.
We work with the UK business security specialist Bulletproof and industry expert Pentest People to provide you with innovative, effective cybersecurity solution. Enquire today for a quote and keep your business protected.
- Proactive security – Identifying vulnerabilities before cyber criminals can exploit them.
- Compliance assurance – Ensuring businesses meet standards like ISO 27001, PCI-DSS, and GDPR.
- Expert-led testing – Combining automated tools with manual testing for deeper analysis.
- Cost-effective risk reduction – Preventing costly breaches and downtime.
- Ongoing security improvement – Providing continuous monitoring and support.
Penetration testing FAQs
What is a penetration test?
It’s a security assessment that identifies vulnerabilities in your organisation’s internal and external network infrastructure. The test helps uncover weaknesses that attackers could exploit, such as misconfigurations, outdated software, and insecure network protocols.
What is a standard penetration test?
A standard penetration test is a controlled security test where ethical hackers simulate real-world cyber attacks to find and fix vulnerabilities in your systems, applications, or networks. It typically follows a structured approach to assess security risks and improve defences.
What is an external penetration test?
An external penetration test focuses on identifying vulnerabilities in internet-facing assets, such as websites, email servers, and cloud environments. This type of test helps protect against hackers attempting to breach your organisation from the outside.
What’s the difference between pen testing and vulnerability scanning?
Vulnerability scanning, sometimes called automated penetration testing, uses scanning software to methodically and simply scan for a list of known vulnerabilities. Penetration testing on the other hand uses in depth analysis and human ingenuity to uncover security flaws that can’t be found by vulnerability scanning alone.
Automated testing and vulnerability scanning are an important part of your defences, such as helping regular patching, whereas a penetration test provides detailed reporting and remediation advice from cyber security experts. Penetration testing companies will use both tools in their arsenal to make sure your business is protected against cyber threats.
What is API penetration testing?
API penetration testing assesses the security of application programming interfaces (APIs) by identifying weaknesses in authentication, authorisation, and data handling. This helps prevent unauthorised access, data leaks, and API abuse.
What tools are used for penetration testing?
Penetration testers use a combination of automated and manual tools, including industry-standard software like Metasploit, Burp Suite, Nmap, and Nessus. These tools help scan for vulnerabilities, exploit weaknesses, and provide detailed reports on security gaps.
What’s the difference between penetration testing and red teaming?
Penetration testing and red teaming are both cybersecurity assessments but differ in scope and objectives. Penetration testing focuses on identifying and exploiting vulnerabilities in a specific system, application, or network within a limited timeframe, providing a report with remediation steps. In contrast, red teaming simulates real-world attacks across an organisation’s entire security posture, including people, processes, and technology, to test detection and response capabilities over a longer period. While penetration testing helps organizations find weaknesses, red teaming evaluates how well they can withstand and react to sophisticated threats.
